Azure Devops
In order to let the Azure Devops pipelines to connect to EKS for deployment the yaml file , we required to create a set of Kubernetes resources in the Kubernetes Cluster:
Create a service account in a namespaces;
Create a custom role with some custom permissions;
Create a role blinding for a service account;
Create a secret associated with the service account
Fowling are the yaml files prepared to create the resources required.
# eks_role.yml
# Create a custom role with some custom permissions
kind: Role
apiVersion: rbac.authorization.k8s.io/v1
metadata:
namespace: python
name: eks-depolyment-role
rules:
- apiGroups: ["*","apps","extensions"]
resources: ["*"]
verbs: ["get", "list", "watch", "create", "update", "patch", "delete"]
# eks_rolebinding.yml
## Create a role binding for a service account
kind: RoleBindingapiVersion: rbac.authorization.k8s.io/v1
metadata:
name: eks-deployment-binding
namespace: python
subjects:
- kind: ServiceAccount
name: eks-deployment
namespace: python
roleRef:
kind: Role
name: eks-depolyment
apiGroup: rbac.authorization.k8s.io
# eks-role-secret.yml
# Create a secret associated with the service account
apiVersion: v1
kind: Secret
type: kubernetes.io/service-account-token
metadata:
name: eks-deployment-secret
annotations:
kubernetes.io/service-account.name: "eks-deployment"
With the yaml file are ready , we can proceed to create the resources using kubectl to run the following:
# Create Service Account
kubectl apply -f - <<EOFapiVersion: v
1kind: ServiceAccountmetadata:
name: eks-deployment
namespace: python
EOF
# Create role
kubectl apply -f eks-role.yml
# Create Role Binding
kubectl apply -f eks-rolebinding.yml
# Create secret associated with the service account
kubectl apply -f eks-role-secret.yml
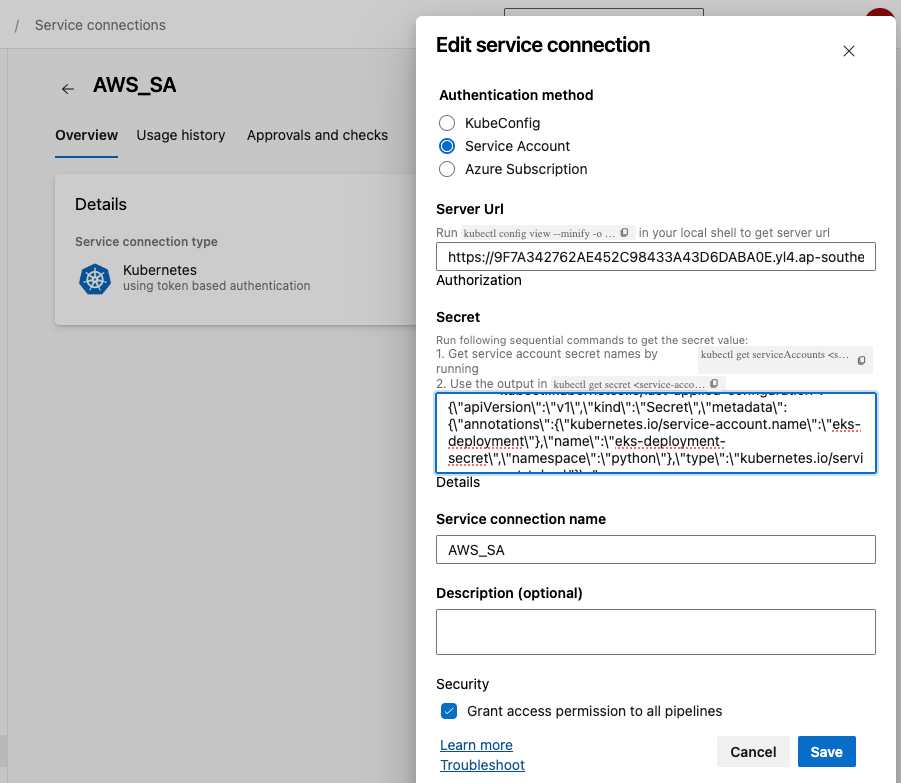
We proceed to setup the service connection in Azure Devops
Run below in local shell to get the server url
kubectl config view --minify -o jsonpath={.clusters[0].cluster.server}
For the secret of the service account , Run below to the service account token and paste the output
kubectl get secret eks-deployment-secret -n python -o json